How To Secure WordPress – Step by Step Guide (2024)

The ultimate WordPress security guide that covers everything you need. Learn how to secure your website the right way using this step by step guide. Go from absolute beginner to advanced today!
A brief overview can be found directly below the table of contents.
How To Secure WordPress?
- Secure your network and devices.
- Use a well-known secure hosting provider.
- Use strong passwords and avoid the “admin” username.
- Limit failed login attempts by installing a plugin.
- Harden your HTTP security headers.
- Add two-factor authentication (2FA) to your WordPress.
- Keep your WordPress core, themes, and plugins up to date.
- Keep your server and PHP version up to date.
- Use a perfectly-coded secure WordPress theme.
- Schedule full cloud backups.
- Use CDN and configure a firewall.
- Install a valid SSL certificate.
- Arrange daily malware scans.
- Block fake crawlers and comment spam.
- Optimize your database regularly and check your file permissions.
- Only install the plugins that you absolutely need.
- Consider installing a security plugin if you are a beginner.
- Consider hiring an expert security company for best results.
WordPress Security Introduction
If you have an online presence or database, then you know that it should be protected.
In fact, this protection process is the staple of practically every website that offers you features to create your own profile, store information, or media online, set up your own mode of communication, or allow you access to certain features or information. In short, if you have a presence online, most websites allow you to protect it from outside attack or influence.
You might have seen this as you perform a simple task like setting up a new email for yourself. As you enter the password, you are shown how weak or strong the character combinations you use are. You soon find out that even your most creative attempt at a password might be considered “average.”
As technology progresses and we develop innovations, attackers, who can steal your online information, destroy your virtual profile, or simply cause havoc in your online database, have better tools at their disposal. And with better tools, we need better defenses. It is not just about having a strong password; it is about using different techniques and measures to enhance your defenses. In other words, you need to beef up your security.
How does one do that? What can someone choose to do to improve their virtual presence? More importantly, how can you improve the security of a platform such as WordPress?
For that, we have created for you the ultimate WordPress security guide that covers everything you need to fully secure your website, the right way!
Chapter 1 - Most Important WordPress Security Questions
Before we go deeper into the security aspects, let us look at some of the commonly asked questions about WordPress and its security.
1.1 – Is WordPress Secure?
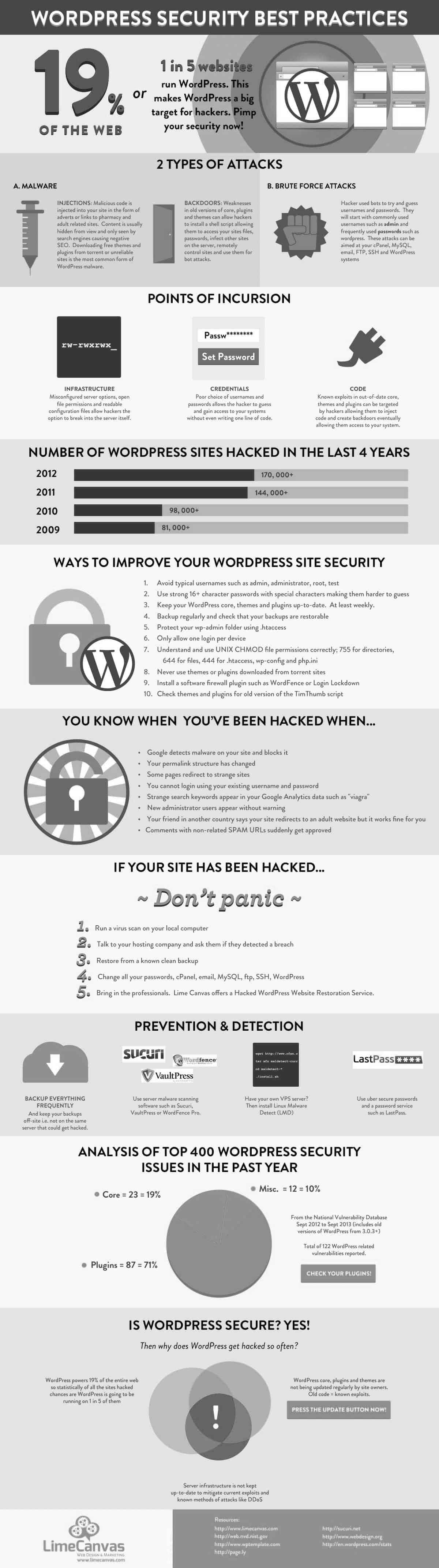
Compared to a lot of options available online, WordPress is one of the most popular ways for someone to build their website. If you look at online stats, then you will find out that WordPress makes up nearly 25% of the total number of sites all over the world. That is a staggering number and that tells us something: WordPress is a platform people trust.
But that means that WordPress becomes a prime target for hackers. Imagine, every one in four websites is made using WordPress. The rate of hackers finding a website that is made using WordPress is pretty high.
Let’s start with some bad news. Every year, hundreds of thousands of WordPress sites get hacked. Pretty scary. Now for the good news.
Most of those sites don’t get hacked because of any vulnerabilities in the WordPress core because that it is robust. Those websites get hacked usually because the creators didn’t follow basic security protocols. WordPress is not at fault here.
So the answer to the question, “Is WordPress safe?” is: absolutely! WordPress is highly secure.
1.2 – How Do I Make My Website 100% Secure?
The truth is, you can never make any website 100% secure (Csutoras, 2018). It is not just about your platform and how powerful it is or what advanced technology it employs. Hackers will always find new opportunities and techniques to break into websites.
WordPress is like any other platform. You can never have a 100% guaranteed solution for providing security to it. But good security is about minimizing risks. It is about taking preventive measures while also being adequately armed to implement any corrective measures.
If anyone tells you that they can secure your website 100%, then they are either lying to you or worse, running a scam.
Never think about getting 100% secure. It’s akin to telling yourself that you have pumped your body with all the known vaccinations in the world and that your body is now 100% disease-protected. That never happens. Nature has a way of proving that.
1.3 – Do I Really Need to Worry About Security If My Website Is Small?
Of course. Everyone needs security. Having the smallest house in the neighborhood does not mean one keeps it unlocked at night in the hope that it gets ignored by intruders.
Even if you have a tiny website with a small amount of information, you need to make sure that you are not leaving it vulnerable to any attacks.
Here is the truth: hackers simply need opportunities to break into a website. According to many hackers and crackers, the act of getting past a website’s security itself is something they enjoy doing. In other cases, your website becomes a conduit, where visitors of your website get diverted to phishing pages and other malicious sites.
Hackers can even make use of your mail server to send spam and malicious software, eventually making it seem as though you are the culprit. Your website can also be used to mine Bitcoin. In fact, hackers can use a false version of your website to send in Trojan viruses to the users. Much harm can be done even if you are using a small site.
Chapter 2 - Top WordPress Security Issues and Vulnerabilities
Here are some ways that your WordPress website can come under attack.
2.1 – Brute Force Attacks
A brute force attack is also commonly referred by another term, brute force cracking. It is the virtual equivalent of someone using multiple keys to try and figure out which one opens a lock.
The entire process of brute force is simple. In fact, hackers don’t have to do a lot of work because all they do is simply allow the computer to use different combinations of passwords and usernames until it finds the right one.
When a brute force attack is in progress, then catching the attackers during the process and neutralizing them is the best response. Once they get into your system, it is going to be more challenging to get rid of them.
Hackers can use brute force attacks to seek access to your WordPress via your login screen.
2.2 – File Inclusion Exploits
File inclusions are actually part of every script for an advanced website. They are needed because they make sure that the code of web applications is kept maintainable and tidy.
They also provide additional features such as allowing web applications to incorporate download functionalities, reading specific files from the file system, and performing various other tasks.
This problem does not happen when you have file inclusions. The problem occurs when you do not implement them properly. File inclusion exploits are one such problem that occurs when vulnerable code is used to load remote files.
These vulnerable codes allow hackers and attackers to find ways into your WordPress’s wp-config.php file.
Let’s just say that the wp-config.php file is one of the most important files in your WordPress installation, and you do not want to hand over control of the file in the wrong hands.
2.3 – SQL Injections
Whenever you create a website using WordPress, then you are making use of MySQL. In short, MySQL is a type of database management system that can be used on a wide range of applications. It is most commonly used for online publishing and web applications.
If an intruder or hacker gets access to your WordPress database, then they have performed an SQL injection. By doing so, they have access to all your website’s data.
How can they exploit this? Hackers and attackers can easily start adding new data to your website. This causes problems not just to your website as a whole, but to the users who visit your website. For example, they can include links to malicious or spam websites.
Hackers can also use SQL injections to cause other forms of damage, such as defacing the website, deleting or stealing data (especially those stored by the users on your server), accessing confidential systems, or even to user accounts, or even compromising certain machines or the entire network itself.
As you can see, a single SQL injection is capable of doing a lot more harm than you might think.
2.4 – Cross-Site Scripting
Cross-Site Scripting, also known as XSS for short, is another form of injection attack and, it is equally as destructive as SQL Injections.
In this process, the attacker or hacker tries to execute numerous malicious scripts directly into the web browser (such as Google, Mozilla Firefox, Safari, and others) of the victim by adding them to the website or web application. When the victims (who are the users) visit the website or web application and perform a certain action, they activate the malicious script, which eventually moves to the browser the victim is using.
Some of the most common delivery systems for XSS scripts are message boards, forums, and webpages that allow users to post comments.
How is it possible to embed XSS into the website and cause such levels of harm? One of the ways that hackers get away with XSS is by using JavaScripts. Why JavaScripts? It’s because they are fundamental to many of the present-day browsing experience. In fact, almost every site that you come across uses JavaScript to some extent. When there is a certain vulnerability to the script, then the hackers can start activating spontaneous JavaScripts in the user’s browser. XSS, like SQL Injection, can also be used to deface a website.
2.5 – Malware
Malware is short for “malicious software,” and everything you need to know about it is in its name. It basically refers to any program or harmful software that causes some nasty effects. They can disable, damage, or invade computers, networks, and devices. They can take either partial control over the designated target or complete control. Either way, they can leave a trail of destruction.
When it comes to WordPress, they can take over the website, extract sensitive information, or even embed themselves into the website. This way, any user who comes to your website inadvertently downloads the malware on his or her computer. You become the source of the malware.
Eventually, when people realize that their computers are being infected, they turn to you, and you are left taking care of damage control just to get everything back to normal.
Typically, when someone says that their website has been hacked, then they are probably referring to a malware attack.
One thing to remember is that malware cannot damage the physical components of the devices (as you might have seen in the movies). They can only cause harm to the data and software components.
But simply knowing about malware is not enough. That is because, at any point, you are at risk of being infected with any one of hundreds of different kinds of malware. Let us look at some of the malware that you are at risk of being attacked by.
2.6 – Types of Malware
2.6.1 – Backdoor
What happens when you are unable to use the main door of your house? You try and check if you have access to the backdoor.
This is essentially the concept behind this malware. When a hacker gets into your system, he or she places a backdoor access. Through this access, they then remove normal access to the system. All the authentication procedures that you had established do not work because they have been taken away from you.
The hacker then has remote access to your system. They can make use of your servers and applications. They can even update other malware into the system and issue unnecessary and harmful system commands.
2.6.2 – Spam SEO
One of the forms of malware that you will come across is Spam SEO. Some people often refer to this as “spamdexing.” These malware target search indexes, so they start including content that they usually shouldn’t.
Essentially, they create or modify web pages to suit the interest of the hacker. This way, the entire web page’s SEO becomes compromised. Imagine that all the effort that you put into developing your website’s SEO simply goes to waste. You might start wondering why your page’s ranking has suddenly become affected.
2.6.3 – HackTool
One of the things about HackTool is that they do not cause harm directly to the computer or system. However, they are like access for hackers to enter into a system and cause all sorts of chaos. One of the primary uses of HackTool is to “crack” certain kinds of software. This means that if you create any content, then the hacker will find a way to duplicate it and sell or distribute it on pirate networks or through illegal channels. It can also forge activation commands and codes. That way, hackers can get into your system and attack it.
2.6.4 – Mailer
Hackers sometimes embed code into the website with the aim of using your website’s email functions. Once they are in control of your email functionalities, they then start sending out spam emails to everyone in your user list. Users have no clue that they are about to open spam. After all, they have been receiving emails from you for quite a while. There should be no reason not to trust you now.
2.6.5 – Defacement
In website defacement, a hacker gets into your website or system and compromises the site’s security. He or she then starts to spread false or harmful messages, create disruptions, cause annoyances, sometimes lower search rankings, or even install malware for the users. Let’s take an example. Imagine that you have an online music store that mainly sells guitars. Suddenly, users open your website and instead of finding useful information about all the cool guitars they can see on your website, they end up seeing pictures of cute cats.
While there is nothing wrong with cute cats (better than any other forms of pictures that could be on there), they are still annoyances because now you have to start putting back the guitar images to all your products and clean out the website for malware.
2.6.6 – Phishing
When attackers want to get personal info out of someone, then they resort to phishing scams or techniques to extract them. Phishing is relatively simple.
You are usually contacted by the attacker online who dupes you into opening a particular email, text message, or instant message. The recipient is then guided into clicking a dangerous link, which can lead to the installation of a particular malware, the freezing of a system because it becomes the target of a ransomware attack, or divulging sensitive information.
Sometimes, the users open a link that takes them to a webpage that closely resembles the page of another website. Unbeknownst to users, the page actually belongs to a hacker who is waiting for the users to enter their personal data on the site.
Chapter 3 - Understanding WordPress Brute Force Attacks
We had earlier caught a glimpse of brute force attacks and the dangers that they can pose. It’s time to look a little deeper and find out more about these dangerous attacks.
3.1 – What Is a Brute Force Attack?
In the complex world of cybercrimes, a brute force refers to a form of attack on a system, database, or website where the hacker uses repetitive and successive attempts on the target to extract password combinations. Usually, the hackers use a specific computer program or bot to carry out the brute force attack, and this particular bot does it vigorously.
It’s as though you have a sophisticated lock on your house’s main door, and someone is using multiple keys to get in. The only difference is that, instead of doing it personally, the person has hired an advanced robot to do the job.
3.2 – How Do Brute Force Attacks Work?
In many cases, hackers install bots in other computers and then link multiple computers together to attack your system or website. By linking systems, they get the combined power of these systems to increase the effectiveness of the attack. But the main concept is that the computer tries to break into a system.
An important note to be made here is that a brute force attack is one of the simplest methods used by hackers or attackers to gain access to a server or site. The main reason for simplicity is that most of the work is being done by a computer.
Let’s take an example right here. Imagine that there is an admin panel that has a two-digit numerical password. If you think about the numbers 0 to 9, then you have 100 combinations to work with. You might need some time, but you can eventually write down all those combinations, and then enter them one by one into the system. Now imagine that the password is a three-digit password. The number of three-digit numbers you can make is 900. That’s a lot of combinations to work with.
Imagine that the password is 12 digits, combined with an alphabet (both uppercase and lowercase) and symbols. Manually it takes thousands of years to cover all these combinations. With a computer, the job gets done way much faster.
Are You Inviting Brute Force Attacks?
Brute force attacks work on your passwords. That’s how they try and get access to your system. But here is the reality of the situation: a computer has to perform millions of calculations to get the right password. It’s not an easy feat. Plugging a password, checking its effectiveness, and then trying another is a long process, made longer by the length of the password and its content.
If you have a weak password, then you are practically serving your website to the hacker on a silver platter.
3.3 – What Are the Top Common Passwords?
Even in this day and age, you would be surprised by the number of people who use some rather simple passwords.
Here is a list of commonly used and easy to hack passwords:
● 123456
● 123456789
● qwerty
● password
● 111111
● 12345678
● abc123
● 1234567
● password1
● 12345
But wait. Wasn’t it mentioned earlier that it would take the computer a while to crack open a code?
Of course, it would. But in almost every case, the computer or bot has already been fed with certain combinations of passwords to try out first. The above list is just some of the options that it works with. Hackers usually have a more extensive list, featuring various simple combinations that they can use.
3.4 – Top Reasons Why WordPress Websites Are at Risk
Understanding some of the common reasons why your WordPress is under attack might help you understand what you should not be doing with your website.
3.4.1 – No Failed-Login Limits
Have you ever tried logging into a MacBook using multiple password attempts? Usually, the system locks itself after three failed attempts. Most email providers automatically shift to a user confirmation page where they try to send across an authentication code to your mobile phone number or ask you a set of security questions to gain access.
These measures are implemented to prevent hackers or unauthorized people from gaining access to your system by using multiple attempts. The more attempts made by someone, the easier it is for them to narrow down the ways in which they can access your website.
WordPress does not automatically place a limiter on the number of attempts one can use to access a site. That limit has to be placed by you. Many website owners forget to add these limits, opening themselves up to brute force attacks.
3.4.2 – Default Username for Admin
In the early versions of WordPress, whenever someone created a website and gained admin privileges, they would usually be given the username “admin” by default. Most WordPress owners would leave the username like that without changing it. In fact, there are many WordPress users who still utilize “admin” as their username, not only because it is easier to remember, but because it is what the account is meant for, admin access.
The problem with such a setup is that anyone can easily guess the username.
After all, what use is the password if it cannot match with the right username? Unfortunately, by using the word “admin”, hackers won’t have much difficulty figuring out how to access your system.
3.4.3 – Known Login URL
Another default setting set by WordPress is the URL. Most of the time, it is a rather known extension and comes as the below:
● /wp-admin
● /wp-login
● /wp-login.php
People don’t think those URLs can be changed. But they can, and by creating a new URL, you make that much more difficult for hackers to gain entry into your website.
Once the user enters the personal data (typically in the form of logins, credit cards, passwords, and other such sensitive information), then the hacker has complete control over them.
3.5 – Ways to Prevent Brute Force Attacks
We have seen how hackers can easily gain access to your system. Now, we are going to see some of the ways that you can prevent such attacks or protect yourself better should an attack happen.
3.5.1 – Use Strong, Complex Passwords
Forget 12345 and abcde. Many site owners use such passwords because they are easy to remember. But at the same time, they are easy to figure out as well.
Do you know how certain sites mention that you should ideally use a lowercase character, an uppercase character, numbers, and symbols? There is a reason why they mention that.
Make use of that technique for your WordPress password, as well.
3.5.2 – Check Your Admin URL
You can actually install a special plugin that allows you to change the admin URL of your WordPress. You can use any random combination of words for the URL. You don’t have to make the phrase coherent, as long as it is complex and confusing. But make sure you note down the URL somewhere in case you might want to refer to it in the future.
Additionally, check the plugin you are going to install and see if it is something that has gotten good reviews and is trusted by people around the world.
3.5.3 – Don’t Reuse Passwords for Multiple Accounts
Even though you have a complex password, do not use it for multiple accounts. Each account should have its own unique password combination. If you feel that remembering all the passwords is a tricky scenario, then make sure that you note down the passwords somewhere only you can access.
3.5.4 – Change Your WordPress Username from Admin
“Admin” is easy to remember. Unfortunately, “admin” is also easy to hack. It’s like someone naming their newborn son “son.”
You know that you are the admin. You don’t need the word to confirm that. Change it. Make sure you put something unique. It doesn’t matter if it is IronMan or DomainMaster. Use anything other than the word “admin”.
3.5.5 – Limit Failed Login Attempts
If you discovered that someone was trying to unlock your front door using a set of keys, what would you do? Your first instinct would be to call the cops or perhaps take your trusted baseball bat and show the would-be intruder why you were called the hardest hitter in college.
In the same way, adding a limit to the login attempts is like telling the system to stop the intruder before he or she gets access to your system.
Check up our Restrict Login Attempts plugin, which automatically covers this task for you.
3.5.6 – Adding Two-Factor Authentication to WordPress
Two-Factor Authentication, or 2FA for short, allows the one accessing the site or system to go through another layer of Authentication so that the right person can be given access.
The reason why this system works is for two important reasons:
The user has to provide two different access codes in order to gain access.
The second code is never fixed in advance. It is an arbitrary number that can be sent to the user. Most second codes only last for a short duration, and they must be used within that duration. Once the timer runs out, the user has to request a new code. Because this code is generated arbitrarily, it makes it much more difficult for brute force attacks to succeed.
2FA also acts as a defense against phishing techniques. Let us assume that the user fell prey to a phishing scam, and now the hacker has the user’s access. However, the hacker still won’t be able to use those credentials unless they can go past the second layer of security. Only the user will be notified of this second layer of security. If the user discovers someone else trying to access the system, he or she can immediately take corrective actions, such as changing the username and password.
There is a good number of plugins on WordPress.org that can help you in implementing that.
3.6 – Tips to Protect Your Website from Brute Force Attacks
It is vital that you use the above methods to protect your website from brute force attacks. However, here are some other tips that you can use as well.
3.6.1 – For WordPress Users
● Do not use the same password for every website. Each website should have its own unique password. That way, if a hacker gains access to one platform, then he or she won’t be able to get access to all of your accounts.
● Rather than using a password, why not make use of a passphrase? For example, you could try YellowChocolate#56CadillacFi$h. Or maybe even the words to your favorite song, such as 3ye0FTh3TigER. This gives you a lot of options to work with. You could use your favorite movies, a phrase you use at home, or even something you are known to say frequently. The idea, however, is to make sure that the words are complex and feature characters, numbers, and symbols.
● Don’t keep your passwords short. You should have at least 12 characters in your password. Some people have gone so far as to use 20 characters. Remember that the bigger your password, the more secure your system is.
● Keep changing your password. Some people have the same password for years, and that only makes it easier for brute force attacks to be successful because eventually, they might just figure out the password. If you change them regularly, then you are throwing the bot or computer off course frequently.
3.6.2 – For WordPress Admins
● Get rid of the habit of using “admin” as your username. There are more creative names that you can make use of. Do not change it to recognizable names and words. For example, don’t use your first name at the username. Try and create something obscure that only you would know about.
● Add a WordPress security plugin and protect your WordPress even more. One of the plugins that you can make use of is the one that allows you to change your URL. It’s a simple change, but it goes a long way to protecting your system.
● Make sure that you keep your password long. In fact, use a passphrase instead of added security. Make sure that the passphrase is at least 20 characters long.
● Consider using security agencies to make sure that your site is extra secure. With their tools and experience, you can ensure that everything is done right. You can also check also our complete WordPress security solution.
3.6.3 – For WordPress Developers
● The more opportunities you give someone to access your website, the closer they come to access your system. It is best not to tempt your luck. Add in a limit to the number of login attempts that can be made. It is true that, sometimes, it might become an inconvenience when the right user forgets the login credentials. However, that is a small inconvenience compared to the big problem that could be caused by unauthorized access.
● You must have seen some websites ask you to solve a small challenge before they provide you with access to their system. The challenge comes in the form of figuring out the phrase in the picture, ticking the right boxes, or entering the words displayed to you. These challenges are called CAPTCHAs, and they are an efficient way to add extra security for two reasons:
- They act as Two-Factor Authentication, except that you have to solve a small challenge.
- They make sure that the entity accessing their systems is a human and not a bot with predetermined commands.
Chapter 4 - Debunking WordPress Security Myths
If you search through the many blogs and forums on the internet, then you are bound to pick up on WordPress security advice, tips, and recommendations. However, not all of them are true, and not all of them can be applied to improve your security. We are going to look at a few of these myths that seem to prevail despite proof to the contrary.
Myth #1: Hide Your URL
Hiding your URL is usually relevant to (/wp-admin) and (/wp-login). An important point to note here is that it should not be used as a standalone option to improve your security. It is simply an additional feature that should be added to a list of other security measures. In fact, you cannot completely change your URL. It appears as changed because of a plugin that hides the original URL under a new one. Think of it as using a mask to hide your face. You are not actually getting rid of your face now, are you?
When you hide your URL, you are merely obscuring it. This is a process that is commonly known as “hiding backend.” Sure, it will prevent hackers from quickly getting to your URL, but it is not a failsafe method.
Myth #2: You Should Hide Your Theme Name and WordPress Version Number
There is a reason why this method does not work, and that is because bots and hackers are not actually looking for your theme name or WordPress version number when they are looking at the code of your website. They are looking for any vulnerabilities to exploit. So a small part of it won’t make a big difference.
Myth #3: You Should Rename Your wp-content Directory
The wp-content directory contains all the media, themes, and plugins for your website. Some people are of the opinion that changing the directory name will fool hackers. But that is far from the truth. Anyone can easily find out the name change by using developer tools in the browser.
Myth #4: The Site is Too Small for Hackers to Notice
Size does not matter. Hackers are going to look for websites to take advantage of, regardless of the size. There are so many uses and abuses for a site, as we have seen.
Myth #5: WordPress is an Insecure Platform
That is not true. Remember our earlier statistics about how one in four websites are made using WordPress plugin? Here’s the thing: that would not have happened if WordPress hadn’t taken their security seriously.
The reason hackers find it easy to access a website is because of the developer and the site itself.
Chapter 5 - Best WordPress Security Tips and Practices
Tip #1: Limit Failed Login Attempts
By now, you are aware of brute force attacks work. They are actually a form of the trial-and-error method. If they are unsuccessful in one attempt, they go for another and another, and they keep going until they get the right combination for the password.
If you limit the number of failed login attempts your system accepts, then you prevent the brute force attack from making another guess to find the right username and password.
However, with the default setting established by WordPress, anyone can make as many attempts as possible. You have to manually change the settings to put a limit.
Tip #2: Use Strong Passwords
Here is something for you to think about. Let us assume that there is a computer with a four-core i5 processor cracking your password. Here is how long it will take to crack your password, depending on its length:
- 7-character password will take 0.29 milliseconds to crack.
- 8-character password will take 5 hours to crack.
- 9-character password will take 4 months to crack.
- 10-character password will take 1 decade to crack.
- 12-character password will take 2 centuries to crack.
By adding a combination of uppercase and lowercase characters, numbers, and symbols, you make your 12-character password truly difficult to crack. Plus, by adding the other security tips mentioned here, the chances of a brute force attack working is reduced considerably.
Tip #3: Use Two-Factor Authentication
A 2FA is another layer of security that a bot or hacker will have difficulty passing through. This is because the second layer of security is based on you receiving a random code that you have to enter. It is as though you have two passwords where the second password is something that no one knows. In fact, even you don’t know the code until the moment you receive it on your device.
However, two-factor authentication does not have to be only a code. There are three different categories of 2FA.
Something You Know
These are usually predetermined questions that require you to provide an answer. “What is the name of your spouse?”, “Who was your childhood friend?” and “What is your mother’s maiden name?” are all some examples of questions that ask you to remember something you already know.
Something You Have
This is the two-factor authentication that we have been talking about extensively in this book. You need to have a physical object like your phone to receive a specific code or phrase that you need to enter.
Something You Are
You can also make use of features such as biometric scans and Face IDs to recognize who you are. Essentially, they make use of a feature that makes you who you are. The reason that these features work is because no two people have the same set of prints, which is like your body’s own way of giving you a biologically unique password.
There are also different methods or means by which you can use your 2FA. Let us look at some of them.
This process is simple. You receive a code in your email. You simply take that code and enter into the area provided and get access to your system or website.
SMS Text Message/Call Phone
If email is not your thing, then you can get the password sent across to your phone. Some platforms like Google actually prefer to send the code to your phone. In fact, there are other platforms that provide you with two options:
● You can choose to get the code sent to your phone via text.
● You can have an automated voice call your phone and speak the code to you.
Mobile App
When you are using an app, then the option you get is a One-Time Password (OTP) or TOTP code sent across to your phone. In many cases, you might notice that as soon as the code reaches your phone, the application immediately recognizes it and opens the app without having you to enter the code manually.
We recommend Authy or Google Authenticator.
Tip #4: Keep The Software Updated
Software updates are a great way to improve security. This is because as new software features are added, you often find new security measures are added to the update as well.
Additionally, an update always brings in new changes to the system, which take over the older versions. These changes often include patches and bug fixes. They help to remove previous exploits. The more recent your WordPress version is, the more fixes you receive, making it more difficult for bots to brute force their way into your system.
In fact, there are bots that are often looking for older versions of WordPress platforms because it is much easier to gain access to them.
Tip #5: Backup Your Website
Sometimes, despite your best efforts, a hacker might successfully gain access to your website. There is not much you can do at that point. Which is why it is always good to have a backup of your data. That way, even if you become a victim of a hack, you don’t have to rebuild your website all the way from scratch. You can take over from where you stopped using the backed up files.
Here at Labinator.com, we offer a complete WordPress maintenance service that ensures your website gets a full daily backup. Learn more by visiting our specialized WordPress Autopilot page.
Chapter 6 - WordPress Security Guide (Step by Step)
- Step 1 – Secure Your Network: Make sure the network that your devices are using to connect to your website is secure.
- Step 2 – Scan your website for malware: It is crucial to run a scan on your site before securing it to determine if everything is working as expected. There are some plugins that can help, but for the best results, it is always recommended to hire a WordPress security expert to conduct this step for you. You also need to run those scans on a daily or weekly basis.
- Step 3 – Use Strong Passwords: A strong password usually has 15+ characters of uppercase letters, lowercase letters, numbers, and symbols. A strong password should not be a name, username, keyboard pattern, date of birth, a friend’s name, or anything that can be tied or related to you. You can also use a secure random password generator to help you in finding the right combination. A good one can be found here.
- Step 4 – Install SSL Certificate: Your web hosting provider should be able to help you with this task by installing the right SSL certificate. A good web hosting provider that offers Free SSL certificates is HostArmada.
- Step 5 – Use Secure Valid WordPress Themes: The default free WordPress themes are trusted and competent, but if you need a premium feature-rich valid accessible theme, you can check our WordPress Marketplace.
- Step 6 – Update Your Theme & Plugins: You always need to keep your themes and plugins up to date.
- Step 7 – Manage Inactive Plugins & Themes: Delete any inactive plugins that you are not using. The same goes for WordPress themes except for the latest default WordPress theme, which you can keep as a fallback.
- Step 8 – Arrange Daily Cloud Backups: Backups are mandatory for all businesses. There are many backup plugins available for WordPress, but they might not be the most reliable option. Some hosting providers help in arranging backups like HostArmada. Our team also provides a complete management service with backups which you can access by clicking here.
- Step 9 – Harden Your HTTP Security Headers: HTTP security headers can provide another layer of security by helping to mitigate attacks and security vulnerabilities. A good website that you can use to scan your HTTP response headers can be found here.
- Step 10 – Brute Force Protection: Installing a Login DDoS Guard plugin can significantly help with this task. In addition to that, you also need to add a Captcha to all forms, including the login and registration ones.
- Step 11 – Install Firewall: Using a CDN like Cloudflare allows you to set several firewall rules that match your needs. There are also some good firewall services online that you can choose from. Our complete security service has this feature included for you as part of the service.
- Step 12 – Filter & Prevent Comment Spam: We have a dedicated extreme spam blocker WordPress plugin that can help you with this task.
- Step 13 – Enable 2-Factor Authentication: This will improve the security on your site and prevent many possible brute force attacks. There is a good number of plugins on WordPress.org that can help you with that.
- Step 14 – Check File Permissions & User Roles: It is essential to check the file permissions on your server if they are all right along with the list of your users and their roles. Ensure that everything aligns with your intentions.
- Step 15 – Conduct Speed & Technical Analysis: It is also advised to speed up your WordPress website and conduct a technical SEO audit for it. By completing those two tasks, you will discover many issues on your site that are affecting its performance and may even compromising its security in some cases.
- Step 16 – Use CDN: Cloudflare is a great free content delivery network that you can leverage to your advantage. It adds a very good security layer to your website. There are also other CDNs available, but most of them are paid ones.
- Step 17 – Use Security Plugins: Installing a trusted WordPress security plugin can significantly help in improving your WordPress security. There are some free trusted ones on the plugins repository of WordPress.org. We also have our own developed premium security plugin that you can access for life when you order our complete WordPress security service.
Chapter 7 - Hire WordPress Security Experts
It is always advised to hire a specialized security agency to handle your website security rather than doing it by yourself. Especially if don’t have the time or resources to cover it all expertly by yourself.
Here at Labinator.com, we provide a complete all-in-one WordPress security service that cover all your needs. Click the button below to learn more how our security experts can help you!
If you are also interested in a complete WordPress solution that cover all your needs from security, speed, maintenance, backups, monitoring and much more, check up our complete WordPress autopilot service below.
WordPress Guides
Best Collection Of WordPress Guides & Checklists
Our complete and latest collection of WordPress guides and resources that cover everything you need to get the most out of your WordPress website.








Download Them All!
All of our guides will be sent to your inbox